A Journey to Implementing Corporate Security: Tried and Tested Guidance
 By Apratim Ghosh
By Apratim Ghosh
 13th May, 2020
13th May, 2020
Cyber Threat Prevention
Corporate IT Security
Corporate Security Strategies
Cybersecurity Governance
“If you spend more time on coffee than on IT Security, you will be hacked” as said by Richard Clarke, White House Cybersecurity.
Security implementation is of utmost importance and hence, a few guidelines need to be in place to ensure a safe working environment. Due to the current situation, most companies have asked their employees to work from home and that makes security even more important.
A few reasons why security implementation becomes important are:
- Less secure home network and WIFI
- Lack of protection against intrusion
- Less control on browsing habit and being more prone to virus, malware and ransomware attack.
Inovar realized the lack of security measures as well as the lack of security infrastructure as most team members use their own unmanaged devices. We realized that a tool was needed to manage the security with very less complexities but at the same time extendable to an enterprise grade security system. As there was no security expert known to us, we took it on our shoulders to make sure that the system was no longer vulnerable
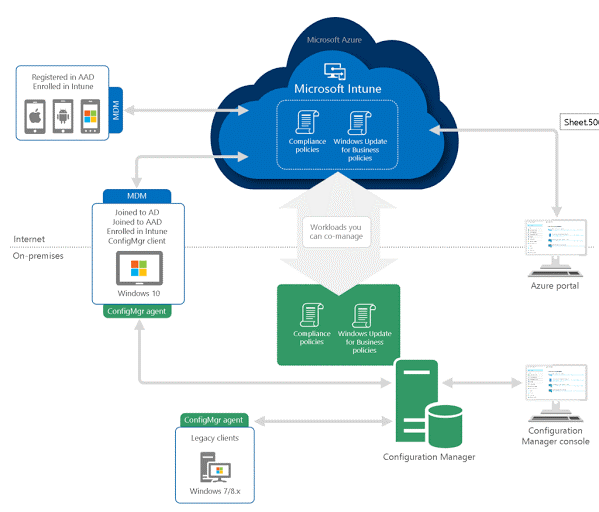
Mobile Device management is used to monitor, manage and secure employees’ mobile devices to ensure the safety of IT infrastructure and there are many tools for it, but does not provide all the necessary functions that are needed. Similarly, tools are available to keep all the laptops and MacBooks compliant with the latest policies and updates. But if we adopt many tools, we must keep in mind, the complexity and cost of implementation.
When the team brainstormed and pooled in their thoughts for an appropriate device management solution, we found tools, most of which were very specific with a certain set of capabilities and were quite costly too. Combining separate tools and per user licenses was intense and the budget was soaring. We then investigated Microsoft 365 and it was quite a mess too, comprising of Intune, Intune for Device, Advance Threat Protection, E5 Security, Azure active directory premium and so on and so forth.
After spending a lot of time on research, we zeroed in on using Microsoft based tools for our cloud infrastructure security. Currently all our team members already use Microsoft 365 E3 licenses and that helped the decision.
After much deliberation, we decided on maximizing the investment on Microsoft 365 and making use of Intune.
This allowed us to:
- Manage everything (Mobile, Desktop, Laptop & MacBooks) via a single console
- Manage all types of devices
- Provide enterprise network security on Windows laptops, which we use primarily.
We are now able to have reasonable command over other platforms and that integrates well with our current platform of Microsoft 365. Another major upside to this was Per User License and so device count per user wasn’t an issue anymore and suited our pockets.
Implementing such a network infrastructure security required humongous effort. A lot of research went into learning about the various security tools and we spent long hours to analyze and plan implementation of the tool. Videos by veterans of this field tried to warn us against using these tools by ourselves or it would take us down. Yes, there is a high possibility, but we were determined to make it work.
We faced many issues during the implementation.
For instance, if we wanted to restrict users from logging into the environment whose devices were not compliant, we needed to get Azure Active Directory premium. After much research, we came across the Exchange ActiveSync feature that helped us block out apps which were not managed. Its not fool proof but covered most of our requirements. After many such workarounds, finally, we came up with a combination that fit our purpose perfectly and we are still currently using it. It provides us with features such as:
- Multi Factor Authentication
- Extensive use of Microsoft 365 Threat management, Data Loss Prevention, mail flow rules and others
- Additional protection on Phishing, Malware and most importantly ransomware.
- Intune with device policies for all (Windows and Mac, Android and iOS phones)
- Exchange ActiveSync capabilities to fine tune permissions on mobile
Using an enterprise grade system at the same time has its demerits. It has so many controls that at a point we were completely lost. There were many ways to approach it but again, coming up with one approach came with its own set of challenges, so we kept trying different options with pilot users till we found an option which worked for us.
Device management is not buying a product on an e-commerce website. One needs to be patient and spend time on it as neither do all changes reflect immediately nor does everything work out at the very first attempt. Do not go looking for just one particular video or blog that will help you set up everything. We went through 50+ blogs and watched around 20+ videos to create our own action plan.
Some of the links are given below to help you out.
But if one is prepared well, one can finally see how easy security in technology has become over time. No system is impenetrable, but I think we have come a long way.
Rightly said by Stephane Nappo (Global Chief Information Officer at Societe Generale International Banking),
“It takes 20 years to build a reputation and few minutes of cyber-incident to ruin it.”
A big thank you to the team for all their hard work and dedication. Everybody should start thinking about implementing security in the new world order. One can start small and move on as per their need. It is not a difficult job to do, as many may think, so start now! Go ahead and implement the same.